|
Security Using Compression-Encryption
Introduction History Lesson: Code Talkers Native American code talkers were deployed by the United States Army during World War II. The most famous role of Native Americans in World War II was performed by the Navajo Indians. They were code talkers, using their own complex native language to help the American troops keep their plans secret from the Japanese. Many codes were used during the war, but the Navajo code was the only one that the Japanese were never able to break. The lesson learned is the communication between the senders and the receivers was coded so no one would be able to break the communication code. With same principle, can compression and encryption be used to create a web and mobile communication code which no one would be able to break? The answer is yes and it is simple, but there are a number of issues which must be resolved: Compression-Encryption speed Decompression-Decryption should speed Build bulletproof Compression-Encryption and Decompression-Decryption Build an infinite number of Compression-Encryption Key and version similar to ID Dynamic updates of both Compression-Encryption and Decompression-Decryption How easily it can be integrated into any existing system The cost of develop and maintaining such processes Can it service the existing World Wide Web (WWW), mobile and any technologies Use Case: Security Using Compression-Encryption Description: According to the Forbes magazine, cyber security is expected to reach $170 Billion by 2020. Cyber security is still a global issue and we believe we a have the answer using Compression-Encryption. We are not the only who would be using Compression-Encryption as a security measure, but our approach and algorithms would be a far more faster, more dynamic and secure communication which is impossible to break. It is easily integrate into any existing system regardless of the technologies. Our approach does not cost much to build or integrate, but marketing it would require serious funding and support. Briefly Describe This Use Case Global Security Issues: It seems that when it comes to security, the experts and the gurus are missing simplicity and they keep adding more layers on the top of what is being done. Looking at starting of the security layers after the Open Systems Interconnection (OSI) which is made up of seven layers. There are HTTPS, firewalls, server security, sockets security (SSL), encryption-decryption, Authentication, Authorization, application security, third party security, other security, database security, plus whatever we did not mention. 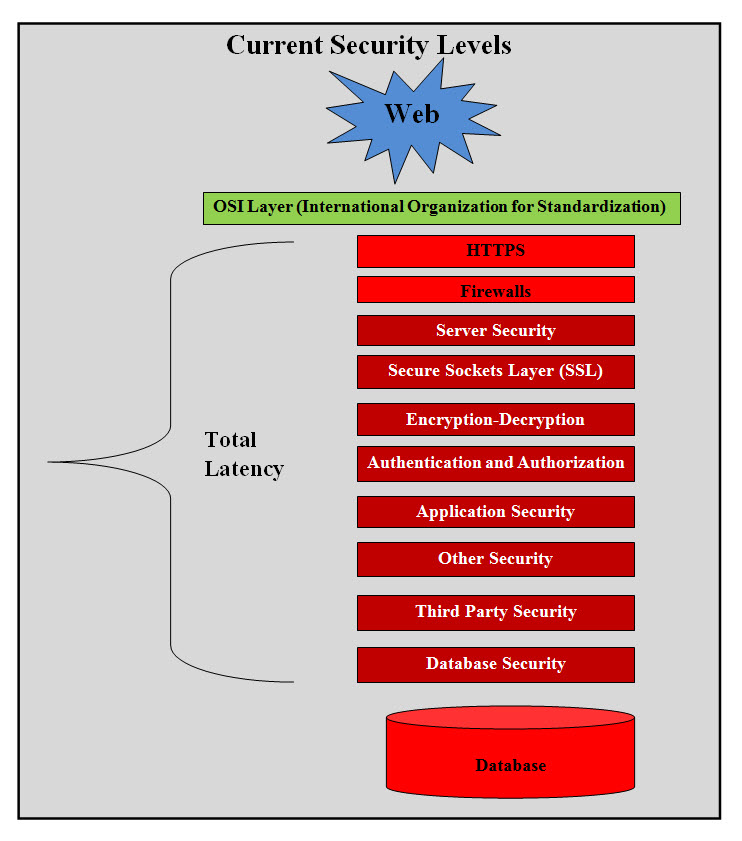
Current Security levels Figure #1 Current Security levels as shown in Figure #1 presents the number of security levels and the latency associated with such structure. This can be simplified with a far faster and more secure structure. Primary Actor: Security is a global issue for everything electronic media, and the actor is every user and system. Goals: Our main goal is to build a permanent practical solution which is dynamic and cost effective. Analysis Despite all these layers and all these measures, hackers (internal and external) are still getting into system and the latest is where institutions are paying ransoms to get their own files decrypted on their own system. From History Lesson-Code Talkers, our analysis is simple by building a communication media which no one would be able to break .Such communication should be cost effective to build and integrated into any system. Architect One-Entry-One-Exit--Chip-to-Chip (C2C) Model: Big Data and security vendors need to look at our proposed Chip-to-Chip (C2C) communication and our One-Entry-One-Exit Model. Critics would be asking about development time and cost, integration, latency and other issues. What we are proposing will eliminate most of the security layers if not all. Communication speed would be extremely faster and latencies would be a fraction of what exists today . We are simply adding to the International Organization for Standardization (OSI) model two chips. An output chip before OSI sending and an input chip after the OSI layers receiving. 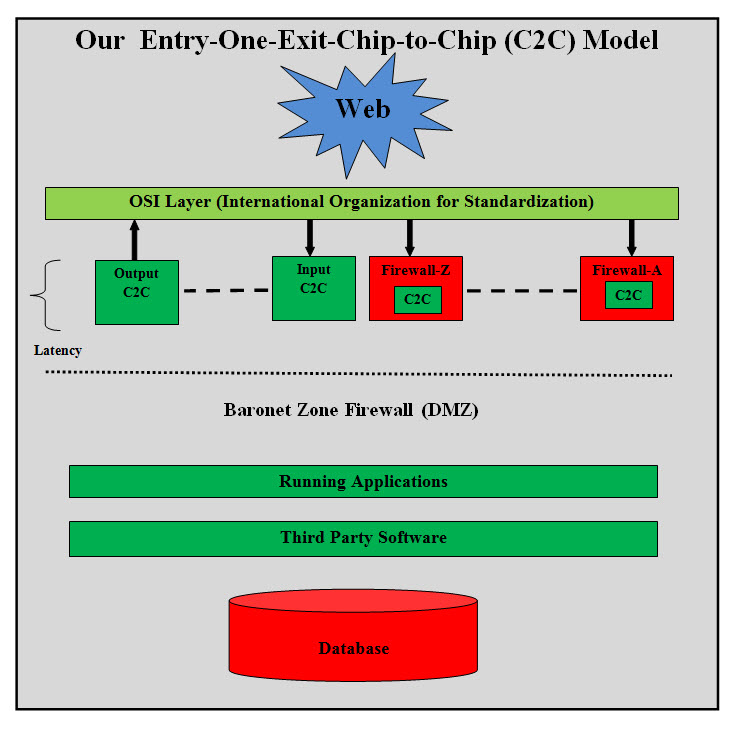
One-Entry-One-Exit--Chip-to-Chip (C2C) Model #2 In short, our C2C will replace or it would be placed into any existing firewalls. The cost of C2C would be minimal to users. The key ingredient to our C2C is our encryption-compression algorithms. C2C will have its own memory, CPU and math-co-processors for performance and speed. Both encryption and compression work on a bit operation and they are executed with astonishing speed. It will run as fast as the CPU and the math-co-processor. Each device such as a server, desktop, laptop, mobile, tablets, TV or any electronic device will have its own unique encryption-compression ID. IDs would be dynamically loaded in the input-output C2C chips. IDs will also be periodically changed. This means for external access, only the authorized ID and IP will have access and will be tracked. This can be integrated and run as a separate subsystem. It would be added as "The Secure Gateway". It will run without interruption or conflicts. For Internal access, critical resources may have its own C2C chip. Every device will have a separate unique ID similar to barcode. The same ID is applied to client-consumer's laptop, desktop, mobile, tablet, TV or any device. For example, a client-consumer's unique ID would be used to access Amazon shopping sites for shopping and his C2C chip will check Amazon's ID(s) for receiving Amazon's web pages on his device. This means that only Amazon pages will be allowed to his device and only his device will access Amazon secured sites. Companies and individuals will have a registered ID. As for privacy, companies and consumers would have "Private ID" as "Unknown". Input and Output Data: Our C2C can be a part of a firewall or a separate device. Regardless of C2C design, it treats input and output data as a stream of bits. Such stream is buffered and analyzed as follows:
Hijacking both ID and IP will not help hackers since they would not be able to produce encrypted-compressed stream. The hijackers' compressed-encrypted stream would produce garbage data. Our compression-encryption is almost impossible to break. No visitor would be able to bypass C2C for the following reasons:
What Differentiate Our C2C from Existing Security Products? Any software team or company can create One-Entry-One-Exit plus compress-decrypt their both the incoming and outgoing data and web pages. They can also apply our One-Entry-One-Exit-C2C model with hardly any issues. Our main advantages are:
Let us look at an example, where medical records such as X-Rays or Digital Parasitological specimens images or any medical records are being shared by several medical centers worldwide. The speed, accuracy, privacy and security are very critical to both these medical centers and their patients. In the case of Epidemics, Pandemics, and Outbreaks of Contagious Diseases, hackers can take these centers and their database as hostages and ask for ransoms. How Efficient is Our Encryption-Compression Algorithms? We have three different algorithms, the first compression is little over 35% lossless, the second is about 45% lossless and best is over 65% lossless. Sadly we cannot give any further information about our trade secrets since there are millions of geniuses and gurus who would be able to use any hint to figure out our trade secrets. |
|---|